 |
Saturday, November 24, 2012
Oracle Database: SQL Fundamentals I
Oracle University | Contact Us: 00 9714 390 9050
Oracle Database: SQL Fundamentals I
Duration: 3 Days
What you will learn
This course introduces participants to the fundamentals of SQL using Oracle Database technology. In this course
participants learn the concepts of relational databases and the powerful SQL programming language. This course
provides the essential SQL skills that allow developers to write queries against single and multiple tables, manipulate
data in tables, and create database objects.
The participants also learn to use single row functions to customize output, use conversion functions and conditional
expressions. In addition, the usage of group functions to report aggregated data is also dealt with. Demonstrations and
hands-on practice reinforce the fundamental concepts.
In this course, participants use Oracle SQL Developer as the main tool and SQL*Plus is available as an optional tool.
This is appropriate for a 10g and 11g audience. There are minor changes between 10g and 11g features in SQL.
Audience
Application Developers
End Users
Forms Developer
Functional Implementer
PL/SQL Developer
Portal Developer
Reports Developer
Technical Consultant
Prerequisites
Required Prerequisites
Familiarity with data processing concepts and techniques.
Course Objectives
Display data from multiple tables using the ANSI SQL 99 JOIN syntax.
Employ SQL functions to generate customized data.
Create reports of aggregated data.
Use the SET operators to create subsets of data.
Run data manipulation statements (DML) in Oracle Database 11g.
Run data definition language (DDL) statements to create schema objects.
Identify the major structural components of Oracle Database 11g.
Retrieve data from tables.
Create reports of sorted and restricted data.
Course Topics
Copyright © 2011, Oracle. All rights reserved. Page 1Introduction
Overview of Oracle Database 11g and related products
Overview of relational database management concepts and terminologies
Introduction to SQL and its development environments
The HR schema and the tables used in this course
Oracle Database documentation and additional resources
Retrieve Data Using the SQL SELECT Statement
List the capabilities of SQL SELECT statements
Generate a report of data from the output of a basic SELECT statement
Usage of arithmetic expressions and NULL values
Implement Column aliases
Describe the concatenation operator, literal character strings, alternative quote operator, and the DISTINCT keyword
Display the table structure using the DESCRIBE command
Restrict and Sort Data
Write queries with a WHERE clause to limit the output retrieved
Use the comparison operators and logical operators
Identify the rules of precedence for comparison and logical operators
Usage of character string literals in the WHERE clause
Write queries with an ORDER BY clause
Sort output in descending and ascending order
Substitution Variables
Use Single-Row Functions to Customize Output
Differentiate between single row and multiple row functions
Manipulate strings using character functions
Manipulate numbers with the ROUND, TRUNC, and MOD functions
Perform arithmetic with date data
Manipulate dates with the DATE functions
Conversion Functions and Conditional Expressions
Describe implicit and explicit data type conversion
Describe TO_CHAR, TO_NUMBER, and TO_DATE conversion functions
Nesting multiple functions
Apply the NVL, NULLIF, and COALESCE functions to data
Use conditional IF THEN ELSE logic
Aggregated Data Using Group Functions
How aggregation functions help to produce meaningful reports?
Use the AVG, SUM, MIN, and MAX function
How to handle Null Values in a group function?
Divide the data in groups by using the GROUP BY clause
Exclude groups of date by using the HAVING clause
Display Data From Multiple Tables Using Joins
Write SELECT statements to access data from more than one table
Join Tables Using SQL:1999 Syntax
View data that does not meet a join condition by using outer joins
Join a table to itself by using a self join
Create Cross Joins
Copyright © 2011, Oracle. All rights reserved. Page 2Use Sub-queries to Solve Queries
Use a Subquery to Solve a Problem
Execute Single-Row Sub-queries
Deploy Group Functions in a Sub-query
Multiple-Row Subqueries
Use ANY and ALL Operator in Multiple-Row Sub-queries
Use EXISTS Operator
SET Operators
What are SET operators?
Use a SET operator to combine multiple queries into a single query
Use UNION, UNION ALL, INTERSECT, and MINUS Operator
Use ORDER BY Clause in Set Operations
Data Manipulation
Add New Rows to a Table
Change the Data in a Table
Use DELETE and TRUNCATE Statements
Save and discard changes with the COMMIT and ROLLBACK statements
Implement Read Consistency
Describe the FOR UPDATE Clause
Use DDL Statements to Create and Manage Tables
Categorize Database Objects
Create Tables using the CREATE TABLE Statement
Identify the data types
Describe Constraints
Create a table using a subquery
How to alter a table?
Drop a table
Other Schema Objects
Create, modify, and retrieve data from a view
Perform Data manipulation language (DML) operations on a view
Drop a view
Create, use, and modify a sequence
Create and maintain indexes
Create and drop synonyms
http://education.oracle.com/pls/web_prod-plq-dad/view_pdf?c_org_id=44&c_lang=US&c_id=D64258GC10
Thursday, November 8, 2012
3DTin is world`s first 3D Modelling tool that runs in a browser
 3DTinDate: 14 Jul 12 - By 3DTin Team - (Free)
3DTinDate: 14 Jul 12 - By 3DTin Team - (Free)
If you ever wanted to introduce yourself into the world of 3D modeling, then 3DTin is one of the best possible ways to do so. Just by visiting 3DTin website, you will instantly be greeted with the powerful 3D editor in which you can design and create anything your imagination can conjure.
This excellent 3D modeling editor was built with the HTML5 code, which enables you to use it on any operating system and modern browser on the current market (Firefox, Google Chrome, Safari, IE9). With the power of WebGL your experience will be smooth and responsive, but even without it you will still have great time.
With 3DTin you can:
Tags: 3dtin review, 3d tin, 3d studio online, models for 3d, animation, sphere, what is 3dtin, modeler, generate, create, online 3d modeling tool, web-based, cloud, web app
This excellent 3D modeling editor was built with the HTML5 code, which enables you to use it on any operating system and modern browser on the current market (Firefox, Google Chrome, Safari, IE9). With the power of WebGL your experience will be smooth and responsive, but even without it you will still have great time.
With 3DTin you can:
- Design models by placing cubes of different colors on top of each other.
- Creat shapes from standard templates (WebGL required)
- Save the sketches in cloud
- Export the sketches in standard 3D file formats - STL, OBJ, Collada
Tags: 3dtin review, 3d tin, 3d studio online, models for 3d, animation, sphere, what is 3dtin, modeler, generate, create, online 3d modeling tool, web-based, cloud, web app
Newway to shop on Facebook
FACEBOOK is testing a service that could drive more of its over one billion users off the web and into physical shops and stores – if only to continue using the web via free WiFi access when they check in with the social media site.
Users who check in via Facebook when entering a store that supports the technology would be directed to that business or brand’s Facebook homepage, where further offers or discounts could be available.
Although Facebook hasn’t officially stated where the trial is taking place or how many businesses are involved, it is understood that rather than being forced to open up their own networks and, therefore, potential malware and other problems topassingcustomers, businesses taking part in the trial will be using special routers provided by Facebook, according to the website InsideFacebook.
The routers will also provide non-Facebook users with access to theWiFi hotspot, via a password.
As well as increasing footfall and passing trade for physical businesses, the feature could also prove to be another boost to Facebook’s mobile ad revenue streams. As more Facebook’s users are nowmobile, the site and its advertisers could benefit from targeting them with localised promotional offers. – AFPRelaxnews
Finding Nemo In 3D Interview
LEE UNKRICH, the vice president of editorial and layout at Pixar Animation Studios, is also an Oscar-winning director for best animated feature on Disney•Pixar’s critically-acclaimed box-office hit Toy Story 3.
He was also nominated by the Academy in the category of best adapted screenplay for his story credit on the film. Unkrich began his Pixar career in 1994 as a film editor on Toy Story and was supervising film editor on A Bug’s Life as well as numerous other Pixar films.
He co-directed Monsters, Inc and the Golden Globe-winning Toy Story 2, before sharing directing credits with Andrew Stanton on the 2003 hit, Finding Nemo. This stunning underwater adventure was produced by
Graham Walters, with an Oscar-nominated screenplay by Stanton, Bob Peterson and David Reynolds.
Teeming with memorable comedic characters and heartfelt emotion, Finding Nemo follows the momentous journey of an overprotective clownfish named Marlin (voiced by Albert Brooks) and his young son Nemo (voiced by Alexander Gould) – who become separated in the Great Barrier Reef when Nemo is unexpectedly taken far from his ocean home to a fish tank in a dentist’s office.
Buoyed by the companionship of Dory (voiced by Ellen DeGeneres), a friendly-butforgetful blue tang fish, Marlin embarks on a dangerous trek and finds himself the unlikely hero of an epic effort to rescue his son who
hatches a few daring plans of his own to return safely home.
Finding Nemo now returns to the big screen in thrilling Disney Digital 3D for the first time. Here Unkrich talks about this new development.
What were your thoughts when you first saw the movie in 3D?
“I was pretty staggered when I saw Finding Nemo in 3D, because we hadn’t designed the film to be a 3D film and it was so amazing to see how much of it looked like we had. “Everything from Bruce the shark lunging at the camera to the amazing scene with all the jellyfish to what is probably my favourite part of the movie in
3D, which is Nemo and his dad going through the coral reef on their way to his first day of school. That scene was so lovely – so colourful and rich in detail – and now there’s a whole new element that really brings it to life and gives it so much depth.”
What makes Finding Nemo such a good film in 3D?
“When we were making Finding Nemo in 2D all those years ago, we worked really hard to give a sense of depth to the images because so much of the movie was taking place in the ocean, in open water – and that could have easily felt very flat. So we did a lot of work to the look of the water to give it a sense of depth.
“Even the scenes in the movie that have nothing in them – when it’s just Marlin and Dory in open water with nothing around them – look cool in 3D because we did so much work putting all these little tiny particles and
bubbles in the water.”
Are there any specific scenes in which 3D really helps express the storyline?
“I was really impressed by the scene in the East Australian Current with Crush and all the sea turtles. We struggled when we made the original film to define that shape in the space – this weird current of water flowing through open ocean.
“The scene with the sharks is really cool, especially when we first meet Bruce, the Great White – he’s lunging at the camera and his teeth are coming right at the audience. It was fun in the original version and it’s really cool in 3D.”
Are you excited that the film will be in theatres again?
“Absolutely. I feel so fortunate to have worked on Finding Nemo and to have helped make a film that generation after generation seems to love. It’s exciting to have it back in theatres again because I strongly believe that the best place to see a movie for the first time is in a movie theatre.
“I’m glad that by releasing it in 3D, a new generation will see it as it was meant to be seen – up on the big screen.
“One of the neat things about 3D is that it can elevate the emotional intimacy with the audience. People get drawn in – it can be a little more intense than when you’re watching a 2D film.
“With Finding Nemo in particular, I think people are going to find that they’re experiencing this world and these characters in a way that they never have before.” – Walt Disney Pictures
THE SUN 2012-11-09 PAGE 21
Thursday, November 1, 2012
Time to grab cyber fraud by its horns
source:http://www.thesundaily.my/news/531356
Posted on 2 November 2012 - 03:07am
KK Tan
INTERNET fraud is causing trillions of dollars in financial losses, time wasted, disruption to work, and much stress and trauma for the victims.
The internet is a double-edged sword which is intended to be used for good but also opens up new possibilities for criminals. With the information superhighway and the efficiency and speed of doing things and business, comes a new risk never seen or anticipated before.
The problem is compounded by greed, stupidity, naivety, fear due to ignorance and a lack of public awareness. There is also the issue of respect for privacy and anonymity over the internet and a great reluctance by the authorities to use an unconventional approach to this problem.
There is a feeling that we need to be extra careful on how to come down hard on the perpetrators as we are in untested waters.
Internet fraud comes in many forms – phishing (the act of attempting to acquire confidential information by masquerading as a bank website or email web host), offers of awards or charity, offers of cheap loans, investment proposals, seeking partners in crime for some frozen funds, seeking dealers for their products, pretending to be potential buyers of products or services, the list is endless.
Practically every unsolicited offer from a stranger on some financial reward or a phishing-type email can be considered a fraud.
Current mass consumer software is not intelligent enough to filter such unsolicited emails. Even a case of "false positive" (filtering out or deleting a genuine email) can result in a lost business or social opportunity. Therefore, many people are compelled to manually check and delete these emails.
What's the catch of these financial offers or rewards? The idea is to half-convince you of the genuineness of an offer and in future, when they feel that they have you hooked, they would then ask you to make some small upfront fee for processing, administration or logistics before you can get the goodies they are offering.
And after your first payment, they will come out with a plausible story to convince you to make another such payment. And because you have already made a payment (and you have therefore "committed" yourself) you are "encouraged" to tell yourself that the deal has to be genuine.
Some of the stories the fraudsters tell you are so good that you have to give them some credit. They are based on research, actual events and facts. The senders often claim to be a relative or an aide of someone famous and important who has died and who left vast sums of money. They need your help to get the money. And for your help, (they promise) millions of dollars in commission.
All these offers and deals have one thing in common – they are too good to be true. Why would a stranger pick you to reward you so well for something anyone can do? But, based on reports, a small but significant number of people still fall victim.
A phishing-type email pretends to be from your bank or the web host of your email and it would normally inform you that it is undergoing some maintenance or upgrade. It would then advise you, with a subtle threat, to provide your password so as to update or reset your account as "failure to do so may result in the termination of your bank or email account".
Or it may say that your account has been suspended and needs you to provide your password to reactivate it. Here, it preys on your fear based on ignorance. No bank or email host would ever ask you to provide your password over the internet. Any such request is deemed to be a phishing email and therefore a fraud.
There has to be a more effective way to address this problem. Let's examine what "ingredients" are needed for such an approach.
First, the solution should be radical because the problem is radical and unconventional. If necessary, we may have to amend the law or policies. Laws are man-made and must evolve to be relevant.
Second, the solution must involve the public. This would also be the best way of educating them.
Third, whatever approach suggested must make it so troublesome and inconvenient for the fraudsters so that it is not worth their while to do it again.
One proposal for the authorities is to get the public to take part in a campaign to respond or reply to such financial offers or phishing-type emails by providing wrong information to the senders based on the assumption that "every single unsolicited financial offer or phishing-type email is considered a fraud, unless proven otherwise".
In fact, the authorities should consider outlawing unsolicited emails but it may be difficult to do so over the borderless internet. Such fraudulent emails can be clearly defined so that genuine businesses using the internet for marketing would not be affected.
Imagine the fraudsters being flooded with millions of emails with wrong information which they would have to spend time, effort and perhaps the right technology to filter and match the information received of say the name, account number and password of a bank account.
And, let's say that every single piece of information they receive does not match. This would frustrate these people and they would wonder if it is worth their effort to do it again.
If the laws or policies are against giving false information over the internet or are not clear, then the authorities should consider amending them to make it explicitly clear that in cases of unsolicited emails on financial offers or phishing-type emails (which are deemed a fraud), the recipient, if he or she wishes to reply, is duty (or legally) bound to supply incorrect information to the sender.
The other positive consequence of such an approach is that the active public participation of such a campaign, with the support of the media, would create much awareness and educate the public about such deceptions. No victim can then say "Oh, nobody told me about it or I was not warned." It would certainly reduce internet fraud.
A radical problem like internet fraud requires a radical approach and a new mindset beyond the walls of our legal and mental constraints.
The writer, the CEO of a strategic consultancy and think-tank firm based in Kuala Lumpur, feels that fraudulent emails are a waste of time and insult people's intelligence. He can be contacted at kktan@thesundaily.com
Microsoft takes on Google, Apple with Windows Phone 8
source:http://www.digitalspy.co.uk/tech/news/a434209/microsoft-takes-on-google-apple-with-windows-phone-8.html
Microsoft has today showcased Windows Phone 8, the new mobile operating system that will become available to consumers this week.
At a launch event today in the US - featuring an appearance from actress Jessica Alba - Microsoft trumpeted the phone software that it hopes will compete with Apple's iOS and Google's Android.

A range of new smartphones running Windows Phone 8 are to go on sale on Friday (November 2), including models by Nokia, Samsung and HTC.
Existing Windows Phone customers will not be able to upgrade to the new operating system, but will instead get access to a Windows Phone 7.8 version, offering some but not all of the features. Microsoft has not yet indicated a launch date for this.
Microsoft's head of Windows Phone, Joe Belfiore, today took a swipe at iOS at the launch event, accusing Apple of creating a rigid format featuring rows of icons with its operating system, a model that, according to him, Google replicated with Android. Belfiore feels that Microsoft's system offers "a truly personal phone experience".
As with previous Windows Phone generations, the unique selling point is 'live tiles': icons that can be placed on the homescreen, and then will update in real-time with new information.

The latest software allows users to adjust the size of these icons, such as reducing them down to thumbnails, or enlarging them so that they stretch across the whole screen.
Users can arrange the 'Start' screen as they choose by 'pinning' their favourite apps, music, games and people to the homepage. Themes on the OS can also be tailored across 20 different colours, including cobalt and crimson.
Microsoft has engineered the Windows Phone 8 lock screen so that it can be integrated with Live Apps. For example, Facebook can be linked to the software so that it displays information such as status updates while the phone is locked.
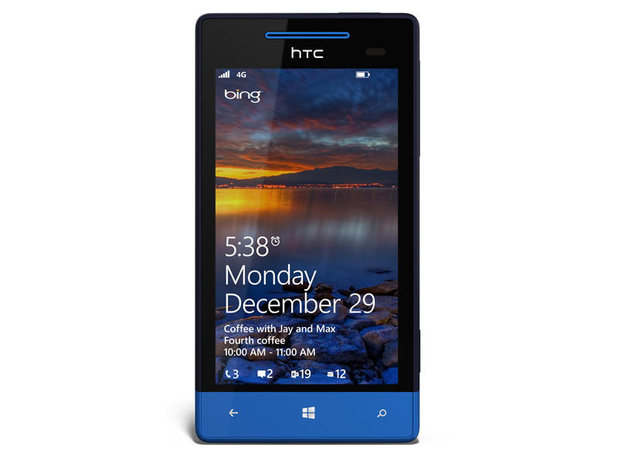
The biggest issue facing Windows Phone in the past has always been apps, as this is where the software is the poor relation to iOS and Android.
Microsoft says that it now has 120,000 apps in the Windows Phone store, a fraction of its competitors' libraries, but the company has signed up 46 of the 50 most popular apps for Windows Phone 8.
New apps coming to the platform include Angry Birds Star Wars, Cut the Rope Experiments, Disney's Where's My Water, LivingSocial, Temple Run, Urbanspoon and Pandora, the internet radio service which Microsoft will offer in early 2013 to customers for an entire year with ad-free music.
However, the absence of the Facebook-owned photo-sharing app Instragram will be disappointing to many users. Instead of Google Maps, the software again runs Nokia Maps.

Other new features on the OS include Rooms, a way to share and chat with a group of other users in a mini, private social network.
Users can share calendars, shopping lists and photos with only those who are invited. The service supports access with users on other smartphone platforms, such as the iPhone, although they don't get the same experience as on Windows Phone.
Kid's Corner is a way for parents to give their children access to their smartphone without them doing anything they shouldn't.
The app, praised at the launch event by Alba, gives kids their own closed interface with only apps approved by their parents. They also get their own camera roll.

Data Sense allows people to manage their mobile data consumption to maximise their tariff plan. It compresses Web images, defers data tasks to free WiFi where available and automatically adjusts the phone usage when the user is close to their data plan limit.
Microsoft claims that the average person will get 45% more web browsing on their data plan by using Data Sense.
Windows Phone 8 also features greater integration of Near Field Communications, including a wallet application for storing debit, credit, loyalty and membership card information for wireless payments and transfers.
The Microsoft-owned Skype will be an "always-on" experience on Windows Phone 8, enabling users to make and receive Skype calls in the same way as a regular phone call.
Friends and family members can be Skype-called direct from the People Hub, and Skype is always on and ready to accept a call.
Microsoft has also integrated Office, Xbox Games and the new Xbox Music service into the operating system, as well as Skydrive, with all users offered 7GB of free cloud storage to place photos, videos, documents and other files.
A range of phones has been produced for the Windows Phone 8 launch - the Windows Phone 8X and 8S by HTC; the Nokia Lumia 820 and 920; and the Samsung Ativ S.
The handsets will go on sale in Microsoft stores and selected retailers this Friday (November 2), with SIM-free pricing to be confirmed at the launch.
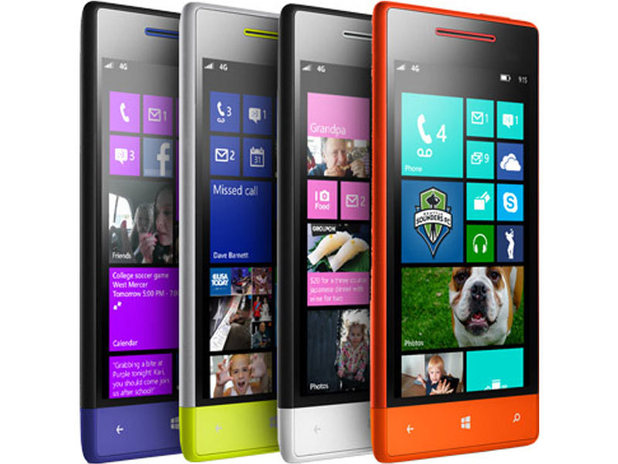
Mobile network EE will exclusively offer the Nokia Lumia 920 in the UK from November 9, including a version that supports EE's new 4G network that goes live tomorrow. EE will also offer the Windows Phone 8X and 8S by HTC.
O2 will offer its customers the Nokia Lumia 820, Samsung ATIV S, and the Windows Phone 8X and 8S.
Three will range just the two HTC handsets, while Vodafone will offer the HTC phones and the mid-range Nokia Lumia 820.
From later this month, retailer Phones4U will sell the Nokia Lumia 920 and Lumia 820, along with the Samsung Ativ S and the Windows Phone 8X and 8S.
The Carphone Warehouse will offer the Nokia Lumia 820 and the two HTC Windows Phones.
At a launch event today in the US - featuring an appearance from actress Jessica Alba - Microsoft trumpeted the phone software that it hopes will compete with Apple's iOS and Google's Android.

© Microsoft
A range of new smartphones running Windows Phone 8 are to go on sale on Friday (November 2), including models by Nokia, Samsung and HTC.
Existing Windows Phone customers will not be able to upgrade to the new operating system, but will instead get access to a Windows Phone 7.8 version, offering some but not all of the features. Microsoft has not yet indicated a launch date for this.
Microsoft's head of Windows Phone, Joe Belfiore, today took a swipe at iOS at the launch event, accusing Apple of creating a rigid format featuring rows of icons with its operating system, a model that, according to him, Google replicated with Android. Belfiore feels that Microsoft's system offers "a truly personal phone experience".
As with previous Windows Phone generations, the unique selling point is 'live tiles': icons that can be placed on the homescreen, and then will update in real-time with new information.

© Microsoft
The latest software allows users to adjust the size of these icons, such as reducing them down to thumbnails, or enlarging them so that they stretch across the whole screen.
Users can arrange the 'Start' screen as they choose by 'pinning' their favourite apps, music, games and people to the homepage. Themes on the OS can also be tailored across 20 different colours, including cobalt and crimson.
Microsoft has engineered the Windows Phone 8 lock screen so that it can be integrated with Live Apps. For example, Facebook can be linked to the software so that it displays information such as status updates while the phone is locked.

© Microsoft
The biggest issue facing Windows Phone in the past has always been apps, as this is where the software is the poor relation to iOS and Android.
Microsoft says that it now has 120,000 apps in the Windows Phone store, a fraction of its competitors' libraries, but the company has signed up 46 of the 50 most popular apps for Windows Phone 8.
New apps coming to the platform include Angry Birds Star Wars, Cut the Rope Experiments, Disney's Where's My Water, LivingSocial, Temple Run, Urbanspoon and Pandora, the internet radio service which Microsoft will offer in early 2013 to customers for an entire year with ad-free music.
However, the absence of the Facebook-owned photo-sharing app Instragram will be disappointing to many users. Instead of Google Maps, the software again runs Nokia Maps.

© Microsoft
Other new features on the OS include Rooms, a way to share and chat with a group of other users in a mini, private social network.
Users can share calendars, shopping lists and photos with only those who are invited. The service supports access with users on other smartphone platforms, such as the iPhone, although they don't get the same experience as on Windows Phone.
Kid's Corner is a way for parents to give their children access to their smartphone without them doing anything they shouldn't.
The app, praised at the launch event by Alba, gives kids their own closed interface with only apps approved by their parents. They also get their own camera roll.

© Microsoft
Data Sense allows people to manage their mobile data consumption to maximise their tariff plan. It compresses Web images, defers data tasks to free WiFi where available and automatically adjusts the phone usage when the user is close to their data plan limit.
Microsoft claims that the average person will get 45% more web browsing on their data plan by using Data Sense.
Windows Phone 8 also features greater integration of Near Field Communications, including a wallet application for storing debit, credit, loyalty and membership card information for wireless payments and transfers.
The Microsoft-owned Skype will be an "always-on" experience on Windows Phone 8, enabling users to make and receive Skype calls in the same way as a regular phone call.
Friends and family members can be Skype-called direct from the People Hub, and Skype is always on and ready to accept a call.
Microsoft has also integrated Office, Xbox Games and the new Xbox Music service into the operating system, as well as Skydrive, with all users offered 7GB of free cloud storage to place photos, videos, documents and other files.
A range of phones has been produced for the Windows Phone 8 launch - the Windows Phone 8X and 8S by HTC; the Nokia Lumia 820 and 920; and the Samsung Ativ S.
The handsets will go on sale in Microsoft stores and selected retailers this Friday (November 2), with SIM-free pricing to be confirmed at the launch.

© Microsoft
Mobile network EE will exclusively offer the Nokia Lumia 920 in the UK from November 9, including a version that supports EE's new 4G network that goes live tomorrow. EE will also offer the Windows Phone 8X and 8S by HTC.
O2 will offer its customers the Nokia Lumia 820, Samsung ATIV S, and the Windows Phone 8X and 8S.
Three will range just the two HTC handsets, while Vodafone will offer the HTC phones and the mid-range Nokia Lumia 820.
From later this month, retailer Phones4U will sell the Nokia Lumia 920 and Lumia 820, along with the Samsung Ativ S and the Windows Phone 8X and 8S.
The Carphone Warehouse will offer the Nokia Lumia 820 and the two HTC Windows Phones.
Tuesday, October 23, 2012
SharePoint Web Application vs Site Collection vs Site vs Sub site
SharePoint Web Application vs Site Collection vs Site vs Sub site Lately I'm playing a lot with WSS and MOSS. It wasn't really clear for me what the difference is between a web application, a site collection, a site and a sub site. This is what I found out. On top of the hierarchy is the web application. In technical terms, this is a web site in IIS (with an application pool associated). A web application needs to have at least 1 Site Collection. The Site Collection is the root site of the web site. Below the Site Collection, there can be one or more Sites. And a Site can contains sub sites.
An overview:
1. Web Application
1.1 Site Collection (SPSite)
1.1.1 Site (SPWeb)
1.1.2 Site (SPWeb)
1.2 Site Collection (SPSite)
1.2.1 Site (SPWeb)
1.2.1.1 Sub Site (SPWeb)
1.2.1.2 Sub Site (SPWeb)
The words between ( ) are the objects of the SharePoint API.
Backup
You cannot backup a web application from within SharePoint. But what you can do is save the configuration in IIS.
With stsadm.exe -o backup -url <site URL> -filename <filename> you can create a backup of a site and all sub sites. And you can restore it with stsadm.exe -o restore -url <site URL> -filename <filename>.
As far as I know there is no built-in option to backup or restore a sub site of SharePoint.
Web Applications
In my case I created three web applications. One for my private SharePoint, one for my blog (new blog soon) and another which allows anonymous access, but IP-filtered. Because each web application of SharePoint is a web application in IIS, you can setup all the security properties of IIS, like IP-based security.
Sharepoint detailed step by step installation
1. Active Directory
add users
-SPSQL
-SPADMIN
-SPFARM
add them to OU
-sharepoint
set spadmin to be domain admin members
2. install Sharepoint Prerequisite
3. install MS SQL 2008 64bit
-add user mydomain\SPSQL for SQL Agent & SQL Engine.
4. open ms sql studio
- security \login \ add user mydomain\spadmin
- server role (dbcreator, public, securityadmin)
5. install sharepoint server
- log in as spadmin
- key : VK7BD-VBKWR-6FHD9-Q3HM9-6PKMX
- select create server farm
- DB server : DCPC\SQLexpress <-- (server name \ ms sql instance)
- DB name : SharePoint_Config
- username : mydomain\spfarm
- password : p@ssw0rd
- pass phrase : p@ssw0rd
- choose ntlm
*ntlm is a suite of Microsoft security protocols that provides authentication, integrity,
and confidentiality to users
*kerberos is a computer network authentication protocol which works on the basis of "tickets"
#While Kerberos has replaced NTLM as the default authentication protocol in an Active Directory
based single sign-on scheme, NTLM is still widely used in situations where a domain controller
is not available or is unreachable. For example, NTLM would be used if a client is not Kerberos capable,
the server is not joined to a domain, or the user is remotely authenticating over the web
-Finish
-IE will open sharepoint. insert username : mydomain\administrator
password : p@ssword
- click no
- cancel
- Central Administration will open.
6. IIS manager review
-open IIS MAnager
-expand DOMAIN
-application pools --> sharepoint central admin : (user-spfarm)
-expand site - this is where central administration site located.
7. Sharepoint create site wizard.
-configutration wizard --> farm configuration --> start the wizard
-user existing managed account
-untick business data connectivity service --> next
-insert title & description -> ok --> Finish
8. review Application Management
-manage web applications --> (sharepoint - 80)
-IE new tab -> type at IE address. http://dcpc/
9. http://dcpc/ Grant Permission
-Grant Permission --> users/groups: domain users --> click 'tick icon'
-ok
10. application management - create new site
-New
-IIS web site Name : SharePoint - IT
port : 80
host Header : it.mydomain.local
Database Name : WSS_Content_IT
-OK
11. DNS
-start -> admin tools -> DNS manager
-domain -> forward lookup zone : right click new host (A or AAAAA)
-Name : it
-IP address : 192.168.1.11 (server IP)
- OK -> DONE
- revirew the create 'it'
- CLOSE
12. Central administration
- Create SIte collection
- web application --> change web application --> share point - IT
- Title : Information Technology Site
- Description : This is a site for IT People
- Primary SIte COllection admin User name : mydomain\administrator
- secondary site collection admin user name : mydomain\spfarm
- OK
- right click it.mydomain.local open in new tab
- OK
13. it.mydomain.local (cannot access)
- start - run - regedit
- HKEY_LOCAL_MACHINE --> SYSTEM --> cuRRENTCONTROLSET --> control --> lsa
- MSV_1_0 (right click ) --> new --> Multi-String value
- rename file (BackConnectionHOstNames)
- right click BackConnectionHOstNames --> modify
- value data :
it
it.mydomain.local
-log in as administrator --> run --> cmd --> iisreset
-log in as SPADMIN
-try again http://it.mydomain.local/
-click site action drop down button
(if is not available add the site to trusted website)
14. it.mydomain.local Grant Permission
-this is where permission can be selected viewer/full/read/contribute
15. sharepoint - IT site review in IIS
-open IIS MAnager
-expand DOMAIN
-expand site - look for sharepoint - IT site.
16. New Site with specific path (sub SITE)
- Central Admin --> web application management
- SharePoint - IT --> Managed Paths
- Type : Explicit inclusion
- Path : home
- check URL
- Add Path
- Type : Wildcard inclusion
- Path : electronics
- check URL
- Add Path
- OK
- central Administration --> Create site collection
- Web application: http//it.mydomain.local/
- Title : ELectronics site
- URL : select /electronics/ & insert etc
- select template: Publishing --> Enterprise Wiki
- Primary ... user name: mydomain\administrator
- secondary.. user name: mydomain\spfarm
- OK
sharepoint installation steps
0. Setup windows server 2008 64bit
1. install AD
2. install sharepoint pre requisite
3. install sql express 2008 64bit
4. install sharepoint 2010
cannot connect to database master at SQL server.xps
Configure a Windows Firewall for Database Engine Access 18 out of 27 rated this helpful - Rate this topic
This topic describes how to configure a Windows firewall for Database Engine access in SQL Server 2012 by using SQL Server Configuration Manager. Firewall systems help prevent unauthorized access to computer resources. To access an instance of the SQL Server Database Engine through a firewall, you must configure the firewall on the computer running SQL Server to allow access. For more information about the default Windows firewall settings, and a description of the TCP ports that affect the Database Engine, Analysis Services, Reporting Services, and Integration Services, see Configure the Windows Firewall to Allow SQL Server Access. There are many firewall systems available. For information specific to your system, see the firewall documentation. The principal steps to allow access are:
1.Configure the Database Engine to use a specific TCP/IP port. The default instance of the Database Engine uses port 1433, but that can be changed. The port used by the Database Engine is listed in the SQL Server error log. Instances of SQL Server Express, SQL Server Compact, and named instances of the Database Engine use dynamic ports. To configure these instances to use a specific port, see Configure a Server to Listen on a Specific TCP Port (SQL Server Configuration Manager).
2.Configure the firewall to allow access to that port for authorized users or computers.
Note The SQL Server Browser service lets users connect to instances of the Database Engine that are not listening on port 1433, without knowing the port number. To use SQL Server Browser, you must open UDP port 1434. To promote the most secure environment, leave the SQL Server Browser service stopped, and configure clients to connect using the port number.
Note By default, Microsoft Windows enables the Windows Firewall, which closes port 1433 to prevent Internet computers from connecting to a default instance of SQL Server on your computer. Connections to the default instance using TCP/IP are not possible unless you reopen port 1433. The basic steps to configure the Windows firewall are provided in the following procedures. For more information, see the Windows documentation.
As an alternative to configuring SQL Server to listen on a fixed port and opening the port, you can list the SQL Server executable (Sqlservr.exe) as an exception to the blocked programs. Use this method when you want to continue to use dynamic ports. Only one instance of SQL Server can be accessed in this way.
In This Topic
Before you begin: Security
To configure a Widows Firewall for Database Engine access, using: SQL Server Configuration Manager Before You Begin Security
Opening ports in your firewall can leave your server exposed to malicious attacks. Make sure that you understand firewall systems before you open ports. For more information, see Security Considerations for a SQL Server Installation Using SQL Server Configuration Manager
Applies to Windows Vista, Windows 7, and Windows Server 2008 The following procedures configure the Windows Firewall by using the Windows Firewall with Advanced Security Microsoft Management Console (MMC) snap-in. The Windows Firewall with Advanced Security only configures the current profile. For more information about the Windows Firewall with Advanced Security, see Configure the Windows Firewall to Allow SQL Server Access
To open a port in the Windows firewall for TCP access
1.On the Start menu, click Run, type WF.msc, and then click OK.
2.In the Windows Firewall with Advanced Security, in the left pane, right-click Inbound Rules, and then click New Rule in the action pane.
3.In the Rule Type dialog box, select Port, and then click Next.
4.In the Protocol and Ports dialog box, select TCP. Select Specific local ports, and then type the port number of the instance of the Database Engine, such as 1433 for the default instance. Click Next.
5.In the Action dialog box, select Allow the connection, and then click Next.
6.In the Profile dialog box, select any profiles that describe the computer connection environment when you want to connect to the Database Engine, and then click Next.
1 of 26/11/2012 12:41 PM
Configure a Windows Firewall for Database Engine Accesshttp://technet.microsoft.com/en-us/library/ms175043.aspx
Community Content
7.In the Name dialog box, type a name and description for this rule, and then click Finish.
To open access to SQL Server when using dynamic ports
1.On the Start menu, click Run, type WF.msc, and then click OK.
2.In the Windows Firewall with Advanced Security, in the left pane, right-click Inbound Rules, and then click New Rule in the action pane.
3.In the Rule Type dialog box, select Program, and then click Next.
4.In the Program dialog box, select This program path. Click Browse, and navigate to the instance of SQL Server that you want to access through the firewall, and then click Open. By default, SQL Server is at C:\Program Files\Microsoft SQL Server\MSSQL11.MSSQLSERVER\MSSQL\Binn\Sqlservr.exe. Click Next.
5.In the Action dialog box, select Allow the connection, and then click Next.
6.In the Profile dialog box, select any profiles that describe the computer connection environment when you want to connect to the Database Engine, and then click Next.
7.In the Name dialog box, type a name and description for this rule, and then click Finish.
[Top]
Did you find this helpful? Yes No
© 2012 Microsoft. All rights reserved.
Friday, October 12, 2012
securecoding.cert.org
https://www.securecoding.cert.org/confluence/dashboard.action
Dashboard
Skip to Recently Updated
Welcome to Confluence
Confluence combines powerful online authoring capabilities, deep Office integration and an extensive plugin catalogue to help people work better together and share information effortlessly.
Subscribe to:
Posts (Atom)


